BGP: Mikrotik RPKI with Routinator
RPKI prefix security with Mikrotik Router OS 7

What is RPKI?
RPKI...offers verifiable proof of holdership of resources's registration by a Regional Internet Registry (RIR).

Utilising RPKI means we can filter invalid IPv6 resources on our border routers, preventing route leaking & hijacks!
Are the commands different on ROS 7 vs ROS 6?
Of course they are!
What do I need to do?
- Set up an RPKI validator,
- Configure our Mikrotik router to speak to the validator, then filter invalid routes.
RPKI Validator
I use Routinator to validate RPKI for my routers. Routinator is written in Rust - and conveniently, runs in a Docker container!

I partially followed another guide for the setup, so full credit there.
Docker-Compose with Routinator
I use docker-compose so I can make environments repeatable. The docker-compose configuration I use:
routinator:
container_name: routinator
image: nlnetlabs/routinator:latest
restart: unless-stopped
ports:
- 3323:3323
- 9556:9556
volumes:
- ./routinator:/home/routinator/.rpki-cache/talsThis docker-compose file uses the latest Routinator image from docker-hub, allows access to the 3323 port (for RPKI checking) and 9556 (for the web client).
A volume is also created for the cache files.
Once you create the docker-compose file, we'll need that Routinator folder. The folder needs to have the UID/GID 1012, so run chown -R 1012:1012 routinator/ to change the permissions.
Once the docker-compose file is created, you can initialise Routinator and accept the ARIN RPA. See the Routinator docs for more info (especially on the accepting RPA section)
docker run --rm -v ~/docker_data/routinator:/home/routinator/.rpki-cache/tals nlnetlabs/routinator init -f --accept-arin-rpaOnce this is done, you can run docker-compose up -d routinator to get the container running, it might take a few minutes to get the required files ready. If you want to see stdout while it prepares, just omit the -d flag.
When the server is up and running, try to access the web interface.
If you check the prefix 2606:4700:7000::/48 with origin AS13335, you should see the test fail.
Testing 2001:4860::/32 with origin AS15169 (a Google subnet and the Google ASN) should pass.
Mikrotik Setup
Note: 1.2.3.4 replaces the local IP address I'm using.
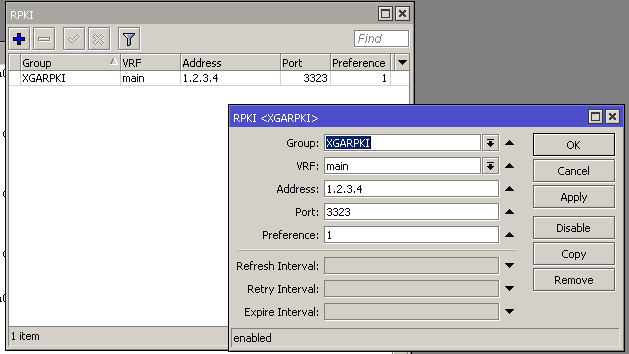
Using your method of choice, configure your router in the /Routing/RPKI options to use the address of your Routinator server. Use the port 3323 unless you changed it earlier.
This is used later during set-up of filtering.
You can test your connection on the command line:
/routing/rpki/session/print
0 group=XGARPKI address=1.2.3.4 port=3323 state=sync version=1 session=49550 serial=207 expires=1h57m5sTesting RPKI before filtering
We can run the command /routing/rpki rpki-check to check the status of a particular route.
Valid (at time of writing):
/routing/rpki/ rpki-check group=XGARPKI prefix=2a05:dfc7:1000::/48 origin-as=205531Invalid:
/routing/rpki rpki-check group=XGARPKI prefix=2606:4700:7000::/48 origin-as=13335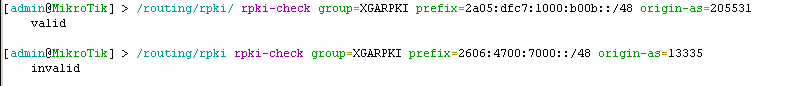
Filtering
Filters will be used by the router to ... filter out ... the invalid prefixes. It's a good idea to test RPKI before setting up the filters, so review the above sections first!
Note below that the group name XGARPKI is used in the filters. There is a space below to add other inbound rules before the accept rule.
/routing filter rule
add chain=BGP-XGA-In disabled=no rule="rpki-verify XGARPKI"
add chain=BGP-XGA-In disabled=no rule="if (rpki invalid) {reject}"
*** add other filter rules here ***
add chain=BGP-XGA-In disabled=no rule=acceptRemember to add your new inbound filter rules to the BGP session when you are finished. When filters are added you may need to re-start your BGP session for them to take effect.
Testing your filters
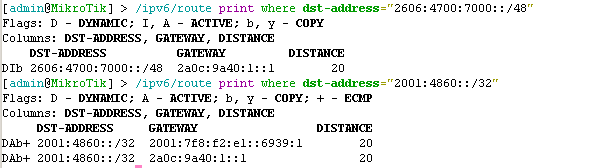
This should be the final check - we want to make sure that invalid prefixes (such as the prefix we tested above) become filtered on the router.
We can do this by running the below command. We should see I included in the Flags. We can also complete other tests using known good prefixes.
/ipv6/route print where dst-address="2606:4700:7000::/48"If you want to be sure this is due to RPKI filtering, you can temporarily disable the new filter rules you added and confirm the bad route becomes active again!